View the latest list of Mimecast Human Risk integrations via the Integration Hub.
Mimecast’s Human Risk Command Center offers customers a comprehensive view into human risk within their organization and gives you the tools to adapt your security posture to tailor protection for those who need it most. With 8% of your users causing 80% of security incidents, organizations must have a comprehensive, real-time understanding of how employees interact with external threats and sensitive data. Mimecast’s Human Risk Command Center is designed to meet this need, and it does so most powerfully through robust third-party integrations.
What is the Human Risk Command Center?
The Human Risk Command Center is a centralized platform that revolutionizes how organizations identify, measure, and manage human-centric security risks. By aggregating data from Mimecast products and a broad range of third-party security solutions, the Human Risk Command Center offers advanced user-level risk scoring and actionable insights that empower security teams to prioritize and proactively address risky behaviors before they lead to incidents. Its integrated security intelligence, adaptive policy controls, and personalized interventions—such as real-time behavioral nudges—enable targeted, evidence-based responses that go beyond traditional reactive security. The Command Center’s unified visibility not only helps prevent costly breaches by highlighting users who pose the highest risk, but also optimizes your organization’s protection policies to continuously strengthen your security posture.
Why Third-Party Integrations Matter
1. Holistic Visibility Across the Security Stack
While Mimecast's portfolio of cybersecurity solutions protects a users work surface, today's organizations run diverse security environments—endpoint protection, identity management, data loss prevention (DLP), phishing simulators, and more. Third-party integrations allow the Human Risk Command Center to collect behavioral telemetry from a wide variety of industry-leading cybersecurity solutions across multiple security domains.
2. Precision Risk Scoring and Response
The more data points available, the more accurate the risk assessment. By correlating events from multiple tools—phishing simulation failures, malware encounters, identity compromise attempts, mishandling of sensitive data—the Human Risk Command Center builds a diverse, individualized risk profile. This empowers security teams to move from blanket policies to targeted interventions, focusing resources where they matter most.
For example:
- A user who consistently fails phishing simulations (from Microsoft Attack Simulation Training or other providers) and also triggers sensitive data alerts in Netskope or Incydr represents a higher compounded risk—and can be prioritized for education or stricter controls.
- Identity risk signals from Microsoft Entra (or other providers) can trigger adaptive policy changes or additional authentication requirements without waiting for a breach to occur.
The more risk data ingested into the HRM platform, the more comprehensive the risk profile for each user.
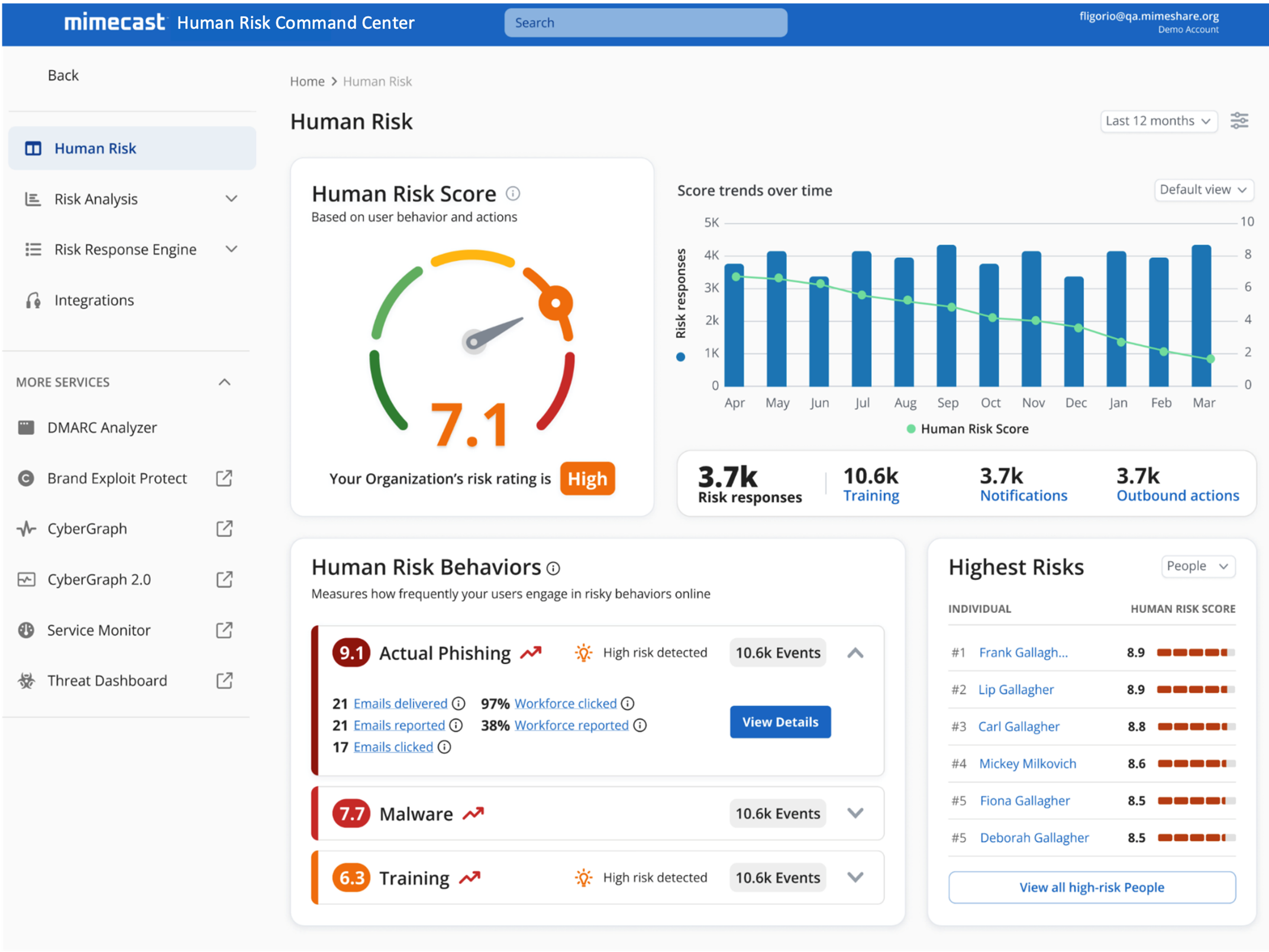
Figure 1: The Human Risk Command Center shows Human Risk Behaviors from various integrations
3. Automated, Adaptive Security Controls
With real-time data from across your security ecosystem, Mimecast’s Human Risk Command Center’s adaptive policies can automatically escalate controls for high-risk users—such as applying browser isolation, increasing phishing defenses, or restricting sensitive data transfers. Integrations with Mimecast products and third-party tools ensure these controls are informed by the full spectrum of user behavior, not just isolated incidents.
4. Continuous, Personalized User Interventions
Integrations enable near real-time behavioral nudges. If a user triggers a malware event in SentinelOne or mishandles sensitive data in Microsoft Purview, Mimecast can instantly deliver context-aware training or guidance, like a behavioral nudge in Slack or Teams, helping change behavior at the moment it matters. This continuous, adaptive approach creates a culture of security awareness far more effectively than periodic, generic training.
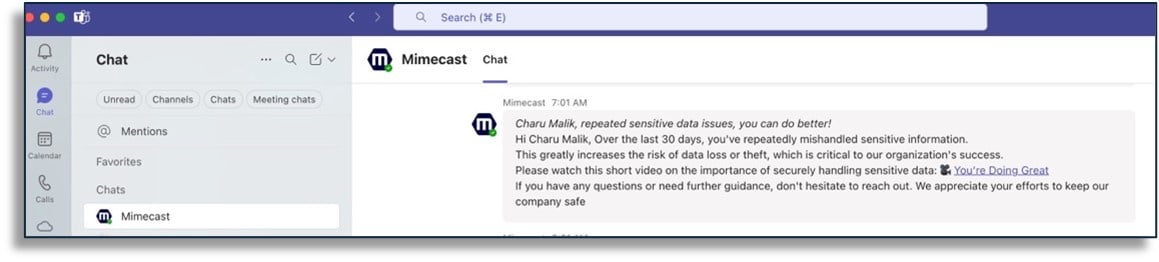
Figure 2: A behavioral nudge delivered to an end-user via Microsoft Teams
5. Unified, Actionable Intelligence for Security Teams
Instead of siloed dashboards and manual correlation, the HRCC presents risk scores, trends, and actionable insights in one place. This reduces response times, eliminates guesswork, and allows for evidence-based decision-making—whether it’s for incident response, policy updates, or compliance reporting.
Integration is Easy – Get Started Today!
Mimecast has designed these integrations to be fast and user-friendly. Most can be deployed in minutes through the Integration Hub, with only basic admin credentials and API permissions required. For information on configuring a specific integration, visit the Mimecast Integration Hub and filter for “HRM Platform” integrations.
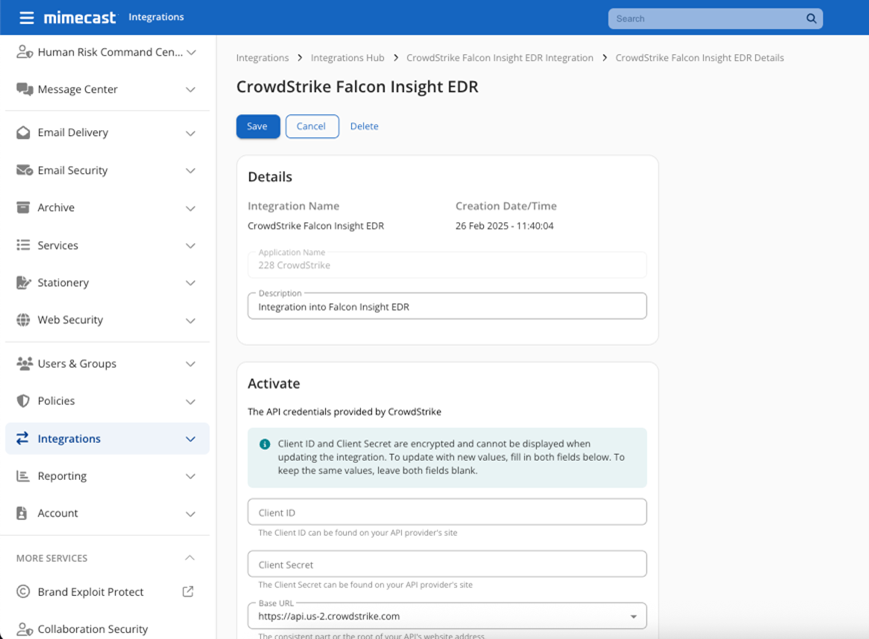
Figure 3: Configuring an integration with CrowdStrike
Conclusion: The Power of Connected Human Risk Management
Third-party integrations are not a luxury—they’re essential for modern human risk management. By embracing an open, connected approach, Mimecast’s Human Risk Command Center transforms fragmented security data into actionable intelligence, adaptive controls, and a safer, more resilient organization. With integrations across phishing simulators, DLP, endpoint protection, and identity providers, Mimecast empowers security teams to see the full picture, act proactively, and drive real behavioral change—before a breach occurs.
To learn more about specific integrations and deployment, contact your Mimecast representative or visit the Integration Hub within the Human Risk Command Center.