Key Points
- Threat actors exploiting SharePoint file sharing services for credential harvesting
- Multi-stage attack chain using compromised accounts and sophisticated evasion techniques
- Campaigns require Ctrl+Click interaction to bypass automated security analysis
- Fake Cloudflare CAPTCHA verification preceding Microsoft 365 credential theft
- Final payload hosted on workers.dev infrastructure
Campaign Overview
The Mimecast Threat Research team has identified an active credential harvesting campaign that abuses Microsoft SharePoint file sharing functionality to deliver phishing attacks. The attack begins with emails originating from compromised Microsoft 365 accounts, lending immediate credibility to the malicious messages. Recipients receive what appears to be legitimate SharePoint document sharing notifications, often from known contacts within their organization or business network. This social engineering approach significantly increases the likelihood of user engagement.
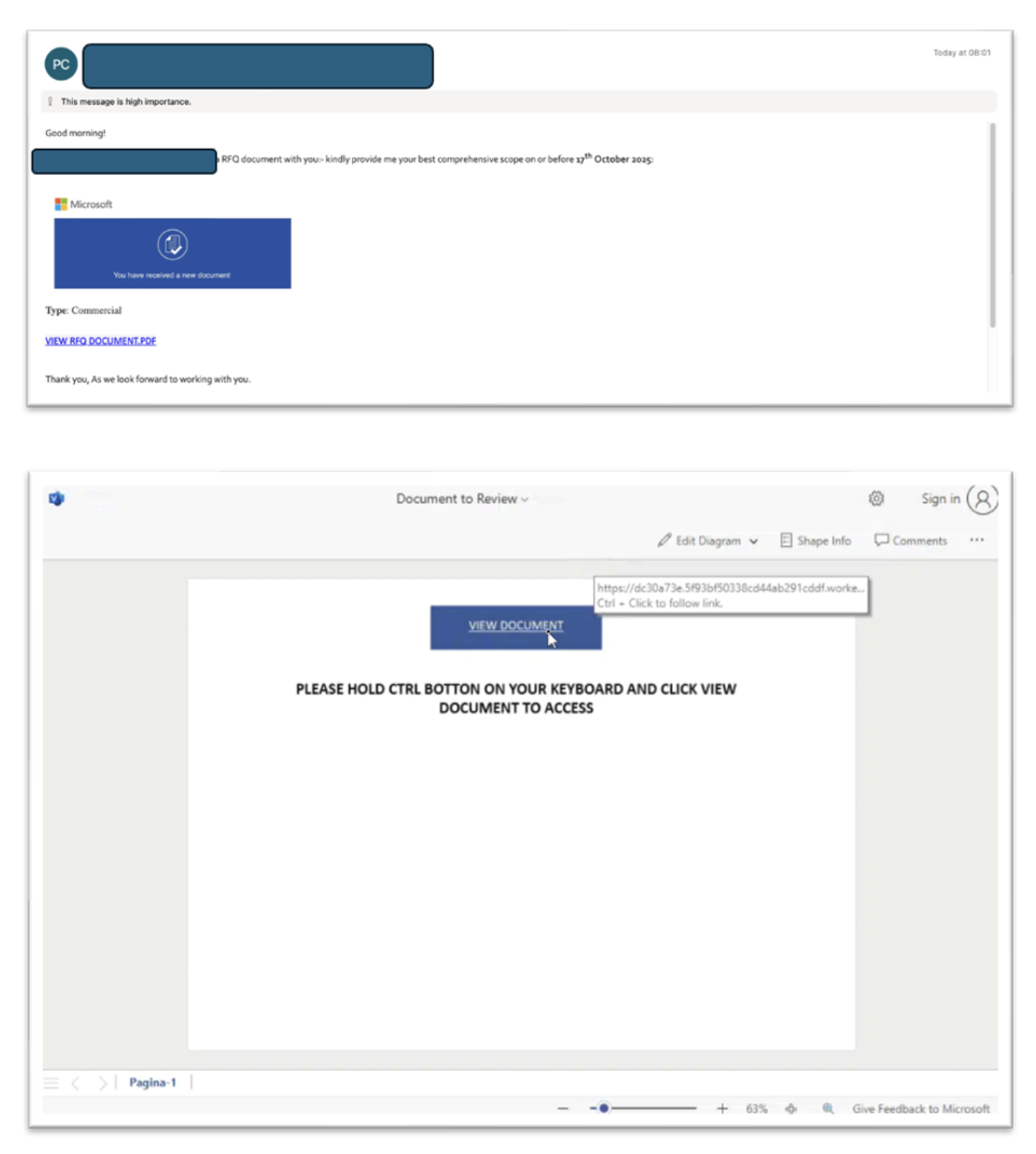
What sets this campaign apart is its implementation of a novel evasion technique requiring users to hold the Ctrl key while clicking the "VIEW DOCUMENT" button. This seemingly innocuous instruction prevents automated security tools from following the attack chain. The requirement appears as "PLEASE HOLD CTRL BUTTON ON YOUR KEYBOARD AND CLICK VIEW DOCUMENT TO ACCESS," mimicking common browser security features. Following the initial SharePoint interaction, users are redirected through a carefully orchestrated attack sequence. The next stage presents a fake Cloudflare CAPTCHA verification page displaying "One more step before you proceed..." with a "Verify you are human" checkbox.
Please click here to read the entire article. We welcome your questions; please ask them by posting a comment below.
Dimakatso Makinta